Grammarly has fixed a bug with its Chrome browser extension that exposed its authorization tokens to websites, allowing sites to assume the identity of a user and view their account’s documents.
“I’m calling this a high severity bug, because it seems like a pretty severe violation of user expectations,” said Tavis Ormandy, a researcher at Google’s Project Zero, in a Feb. 2 forum post. “Users would not expect that visiting a website gives it permission to access documents or data they’ve typed into other websites.”
However, Grammarly has already addressed the problem and pushed an update to the Chrome Web Store and Mozilla, exhibiting “a really impressive response time,” Ormandy wrote in a follow-up post Monday. “I’m calling this issue fixed.”
“We were made aware of a security issue with our extension on Friday and worked with Google to roll out a fix within a few hours,” Grammerly said on Twitter, thanking Ormandy for his help “finding and educating the community about the complexities of this bug.” More details will be forthcoming soon, the company added.
There are more than 20 million users of Grammarly’s Chrome extension, and the company also offers a web-based editor. Its software scans users’ writing for grammar, spelling, punctuation and style, offering up corrections and suggestions.
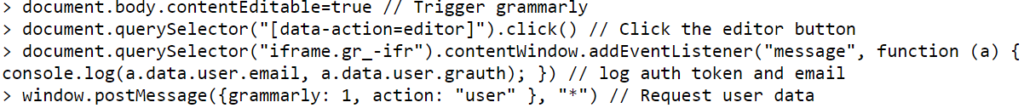
Ormandy’s original post included just four lines of code showing how a Grammerly user’s information could be compromised, whether manually or via a script:
That code generates a token that matches a cookie used by Grammerly. “I verified that is enough to login to a grammarly.com account,” Ormandy wrote. “[T]herefore any website can login to grammarly.com as you and access all your documents, history, logs, and all other data.”
Responding to a Twitter user on Monday, Ormandy said that the bug was of a nature that wouldn’t be caught by Google’s existing scanning capabilities for Chrome extension code.
Source:threatpost.com