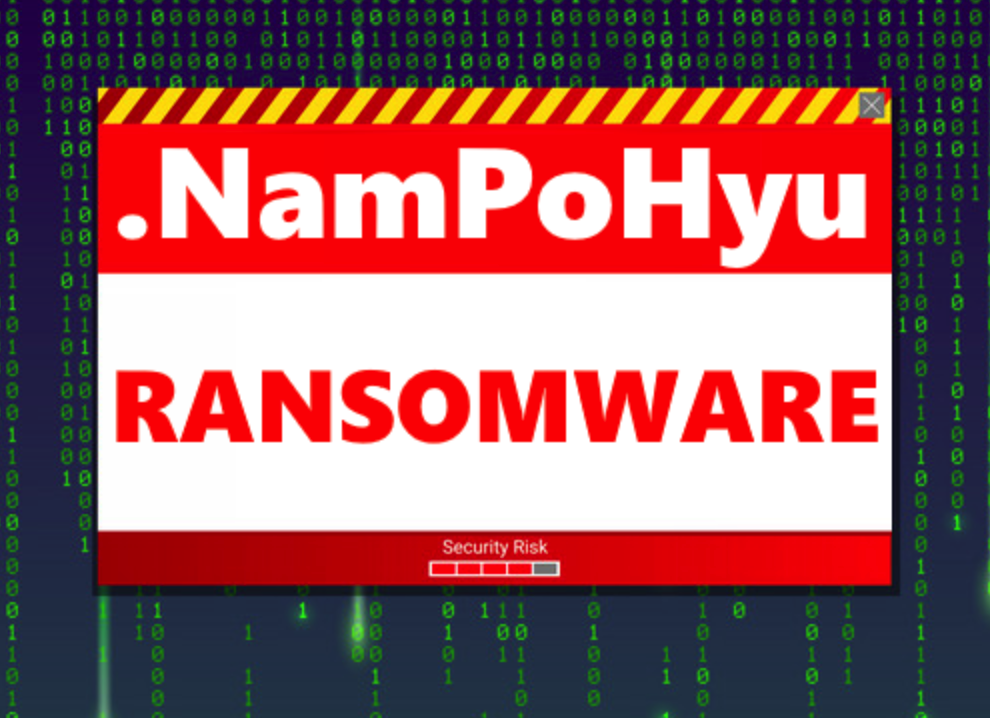
The NamPoHyu ransomware is doing things differently by searching for accessible Samba servers, brute forcing the passwords, and then remotely encrypting their files and creating ransom notes.
A ransomware family was recently spotted targeting vulnerable Samba servers: NamPoHyu Virus aka MegaLocker Virus. NamPoHyu Virus is unlike typical ransomware families that are delivered locally and launched as executables. Instead, it searches for publicly accessible Samba servers, brute-forces them, and runs the ransomware locally to encrypt the exposed servers.
Samba is the standard Windows interoperability suite of programs for Linux and Unix that has been used since 1992. It is an important component to seamlessly integrate Linux/Unix Servers and Desktops into Active Directory environments. It can function both as a domain controller or as a regular domain member.
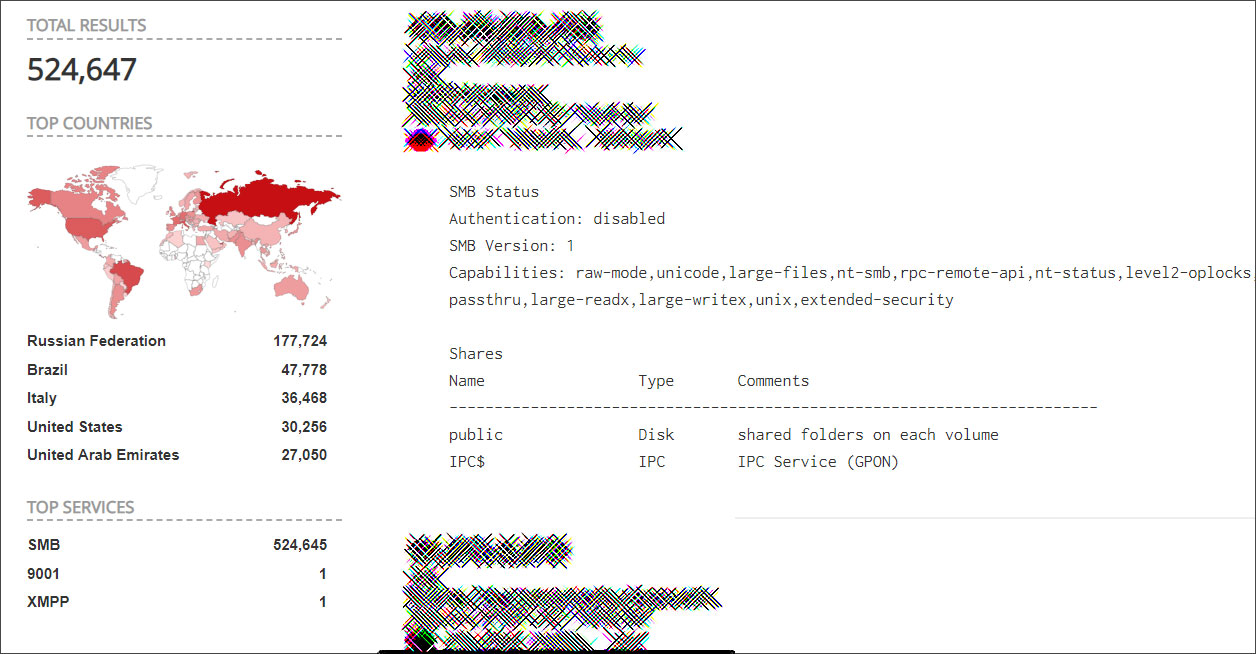
Currently according to Shodan, there are close to 500,000 Samba servers unauthenticated and publicly accessible.
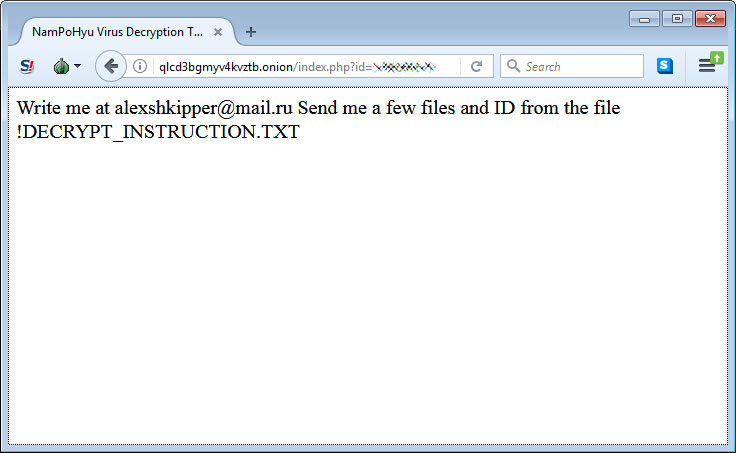
The MegaLocker virus was first found in March 2019 on NAS devices, it uses to encrypt the files and append a .crypted extension to encrypted files. Starting from this April 2019, according to Bleepingcomputer.com, it has been changed to NamPoHyu Virus it uses to encrypt the files and append.NamPoHyu extension to encrypted files.It encrypts the file’s in the system and asks to make ransom payment through Tor site, for personal victims $250 and $1,000 USD in bitcoins for companies. When going to the Tor site, victims are told to email [email protected] with the ID listed in the ransom note for payment instructions.
In order to protect yourself from ransomware it is important that you use good computing habits and security software. The most important step is to always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
You should also make sure that you do not have any computers running remote desktop services connected directly to the Internet. Instead place computers running remote desktop behind VPNs so that they are only accessible to those who have VPN accounts on your network.
Thirdly, it is recommended to use a double layer of protection. In other words, to use two different passwords. Best practise also advise against opening attachments/links that presented in emails received from suspicious, unknown addresses. If received email is irrelevant (even if presented as important) or its sender seems to be suspicious, then the best option is to ignore it.
However if you are infected by the virus, here is a ransomware mitigation checklist and the step by step removal guide.
Sources: gbhackers.com, trendmicro.com